Data backup rule of 3
Perhaps I don’t have to explain why we need backups but just in case, it's really simple.
Our client portal provides all the tools you need to create, view or update your support requests.
For urgent IT support during business hours, or if you suspect anything suspicious call 01314528444 for the fastest response.
If one of our team has asked you to start a remote control session on your computer, use the remote control menu option above.
4 min read
itfoundations
Originally posted on January 22, 2024
Last updated on September 23, 2024
GDPR reminders were everywhere on the countdown to the implementation date. Thereafter, everything went quiet.
However, it hasn’t gone away. But when was the last time you discussed it? Or is it another case of “it’ll never happen to me”? GDPR should have become a standing item on the management meeting agenda in every business.
Our role with data means we have an obligation to help businesses understand the importance of data management, provide the tools to support and make it as easy and effective as possible.
“Data is the new crown jewels of every business today.”
GDPR is too often seen as a tick box exercise, Step 1: Ensure you audit your data and document what has happened in the event of a breach, aiming to demonstrate you did at least try to do something to protect your data. Unfortunately, without further steps, this is a reactive measure and is too little too late.
Add this onto an ever-increasing number of security threats facing businesses and you have a huge risk on hand. Which affects businesses of all sizes, not only major corporations like many believe.
Major vendors are constantly releasing software and updates to improve security and functionality of protecting your data, but this can be a minefield of options and seem overwhelming to implement on an individual scale.
For most businesses, Microsoft remains the main software provider in use, and increasingly businesses Office365 is the de-facto standard of everyday use.
For those non-IT orientated businesses, here are some benefits of using each type of data protection product:
A tool to protect and secure an organisation’s resources and data, providing all the necessary features in one environment in order to keep data safe.
Whilst Office365 alone comes with some options to manage and protect your data. If devices are lost or stolen, we can wipe mobile devices with Exchange Online, create content policy rules and Data Loss Prevention policies in the Security and Compliance, but we can’t manage the device itself.
With Microsoft 365 you get Microsoft Intune included to manage your mobile devices. Intune allows you to control multiple types of devices and business apps used on each. Device policies and application policies (Intune Application Protection Policy (APP)) may also be set to secure devices in a way that works for your business.
Using APP, you don’t need to control the device itself. You can simply apply the policy to the application, for example, Outlook. This means that when Outlook is used it may require a pin code to access any corporate data, check that the device is not jailbroken, or prevent copies of corporate data from being sent to other apps such as personal mail.
Furthermore, the Selective Wipe is a welcome option when your users are working from their own devices (BYOD). Allowing you to remove the managed apps and data while keeping the personal data intact.
It is not only mobile devices that can be managed with Microsoft 365, you also manage and even deploy your Windows 10 devices. Don’t expect a full System Centre Configuration Manager replacement – you can’t install third-party apps with it. But what you can have is Windows 10, and make sure the required Office applications are installed and kept up to date.
Why stop there, you can also configure your Windows Defender, update management and firewall policies with Microsoft 365 if you don’t have a separate third-party endpoint management solution in place.
Keeping your data safe is one part managing your devices and on the other hand, protecting your actual data. Microsoft 365 gives access to multiple tools to help protect data.
Azure Information Protection is one of these tools, designed to protect your data. Based on classifications and protection information, Azure will protect your data no matter where it’s stored. Pretty much in the same way as you can do with most PDF files. You can prevent printing, sharing, editing or copying of those files.
Other features included in Microsoft 365 are Windows Hello, Device Guard and Credential Guard. These features are aimed at strengthening the security of your devices by using virtualization-based security features to isolate your secrets and configurable code integrity policies to protect your devices against unwanted apps or code.
All the options above deal with how you can protect your data using software. These can be either configured to match your existing policies or as a basis to create them.
There is however one rather large area missing here, staff. After data, your staff are undoubtedly the most important asset in the business, and it is imperative that the whole team are educated to understand the great importance of information and data management.
Unfortunately, a quick chat at a meeting or a poster on the wall in the staff room is not enough any more. There needs to be a planned approach to schedule regular training, and updates to ensure every employee clearly understands their personal responsibility when dealing with company information daily.
One of the options for such scheduling is a product called knowbe4. This is a managed approach to training and simulation of threats to staff to keep everyone on their toes. It allows small, bite-size training to be delivered directly to desktops, simultaneously recording how well the staff member completes the training. Training can be followed by simulating a threat or an attack on a user, ensuring they adhere to regulations and avoid clicking on a suspicious link or agreeing to send confidential information in an email for example. Reports can then be easily analysed to know the effectiveness of the training and attacks.
Like all areas of technology, change happens at an incredibly fast pace and it is harder for small and medium-sized businesses who are not technology experts to keep up with this pace. This is why it is imperative to create a trusted partner relationship with a managed IT provider who can guide you through the pitfalls of information management and ensure you have the best practices in place to protect your data and business.
Contact us today to discuss your data management needs.
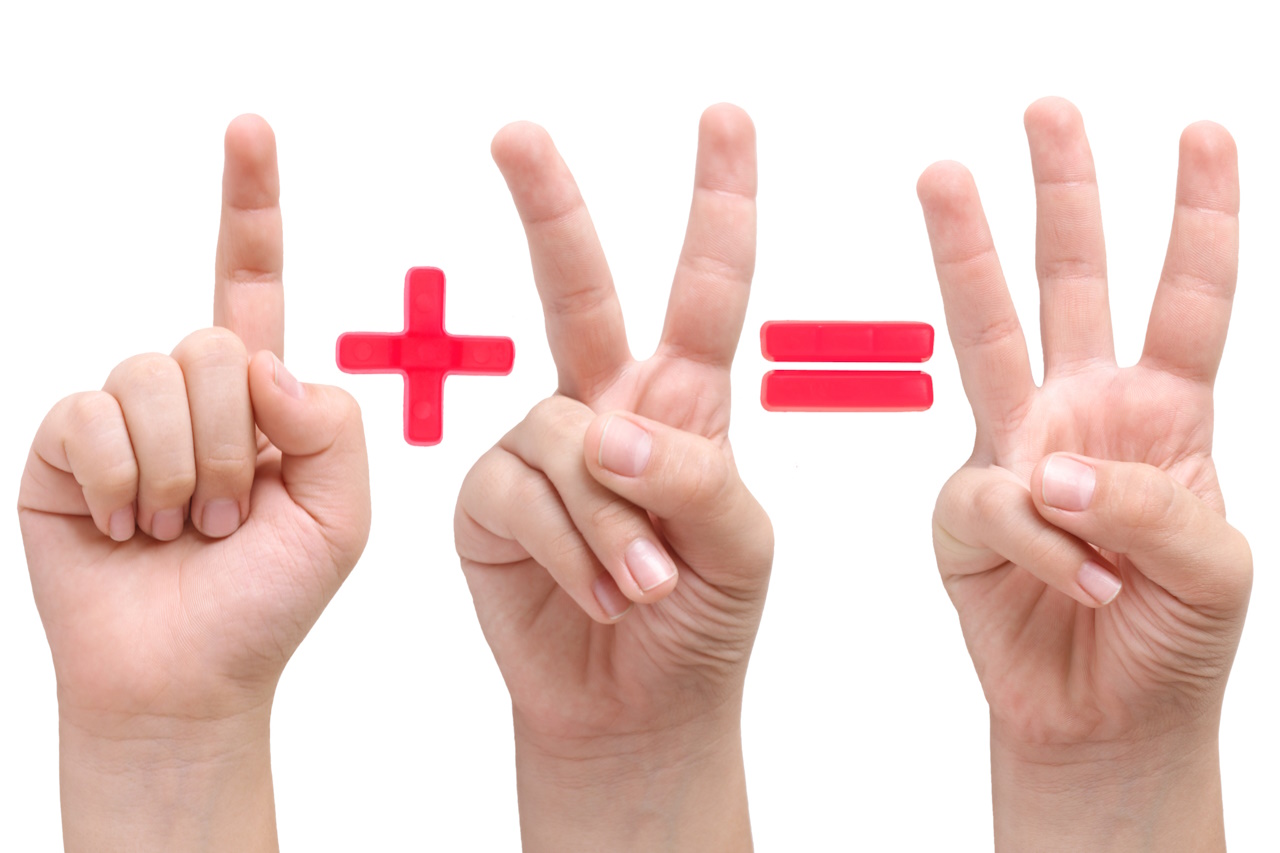
Perhaps I don’t have to explain why we need backups but just in case, it's really simple.

3 min read
The need to backup data has been around since floppy disks. Data loss happens due to viruses, hard drive crashes, and other mishaps. Most people...

Data privacy has been a growing requirement ever since the internet age began. So much personal information is flying around through computer...